
Programming and IT Security

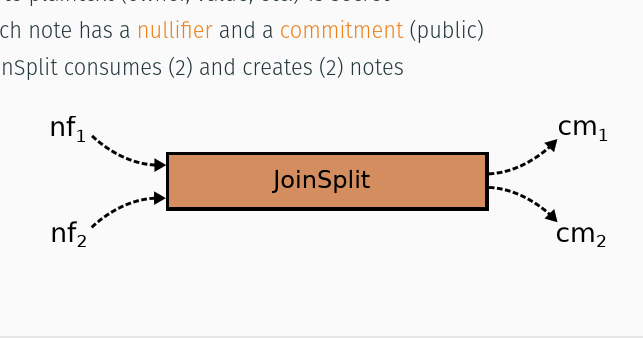 Basics of the "Zcash" cryptocurrency
Basics of the "Zcash" cryptocurrency
Zcash is the third iteration of an extension to the Bitcoin protocol that
provides true untraceability, i.e. fully anonymous transactions. It is
arguably the first serious attempt to establish this extension, in the form
of its own blockchain, beyond the form of an academic proposal. The talk
provides an introduction to the magic that makes it work.
 Iteratees in C (prototype)
Iteratees in C (prototype)
An Iteratee
is a data structure that represents a stream processor. It
consumes a stream of input elements and at some point produces a result or
fails with an error. Streams may consist of elements of any type. Processing
proceeds one chunk of input at a time.
Development of a C library that realizes the concept of Iteratee I/O
which originated in the context of functional programming.
Contains a fast garbage collector of own design, the properties of which are tailored to the case at hand.
Implementation of a simple example (word count) that reaches the run-time performance of its classic equivalent, even slightly surpassing it.
 A small functional compiler (work in progress)
A small functional compiler (work in progress)
The project is to build a compiler for a modern functional programming language
and to get it self-hosting as quickly as possible, bootstrapping from minimal
dependencies.
Building a minimalistic functional programming language in the form of a translator to standard C. The initial version was written in around 500 lines of C and then reimplemented in about 300 lines of the language itself (self-hosting).
Contains a garbage collector of own design, the properties of which are tailored to the case at hand, as well as a flexible test system to check the function of the compiler.
 Functions in different programming languages
Functions in different programming languages
The specific realization of functions and subroutines as provided by six
popular programming languages are surveyed from the standpoint of
language design. The languages discussed are C, Scheme, (Common) Lisp,
Smalltalk, Python, and Scala. Questions of interest include the sharing of
namespaces between functions and other objects, closures and scoping rules,
support for higher-order functions, lambda expressions, etc. An
additional section notes interesting points about some languages that are not
included in the main presentation.
Essay about the different representations of the mathematical concept of functions in several programming languages.
Prepared as classwork for a seminar in computer science.
 Arduino JTAG adapter
Arduino JTAG adapter
The XC9572XL is programmed via a standard JTAG interface. I did not have
anything that speaks JTAG so went looking if my Arduino can be turned into
an appropriate programmer. The solution that I found, however, did not
work; so I built my own.
Development of an Arduino program for the direct interation with micro chips via the JTAG interface.
 Arduino AVR programmer
Arduino AVR programmer
And so my first real Arduino project is an AVR programmer. [translated]
Development of an Arduino program for the loading of other ATmega micro controllers via the proprietary programming interface.
 Mathematical basics of asymmetric cryptography
Mathematical basics of asymmetric cryptography
This talk aims to give a
generally understandable introduction to the
mathematical basics of asymmetric cryptographic algorithms
that form the backbone of modern cryptographic infrastructure.
Participants should be enabled
to judge more than superficially the cryptographic systems
which build upon these primitives.
[translated]
Talk held at the CCC conference SIGINT 2009
. (German)
 Cryptoanalysis of the Siemens & Halske T52
Cryptoanalysis of the Siemens & Halske T52
The Siemens & Halske T52 (in its several variants) [...]
was a teleprinter
with integrated encryption/decryption facility. It was cryptographically
superior to the Enigma and, by its nature, much more sophisticated in terms of
its electro-mechanical engineering.
Essay about the successful decryption of Nazi-German teleprinter traffic by Swedish mathematicians during the World War II.
Originally prepared as classwork for a seminar in mathematics.
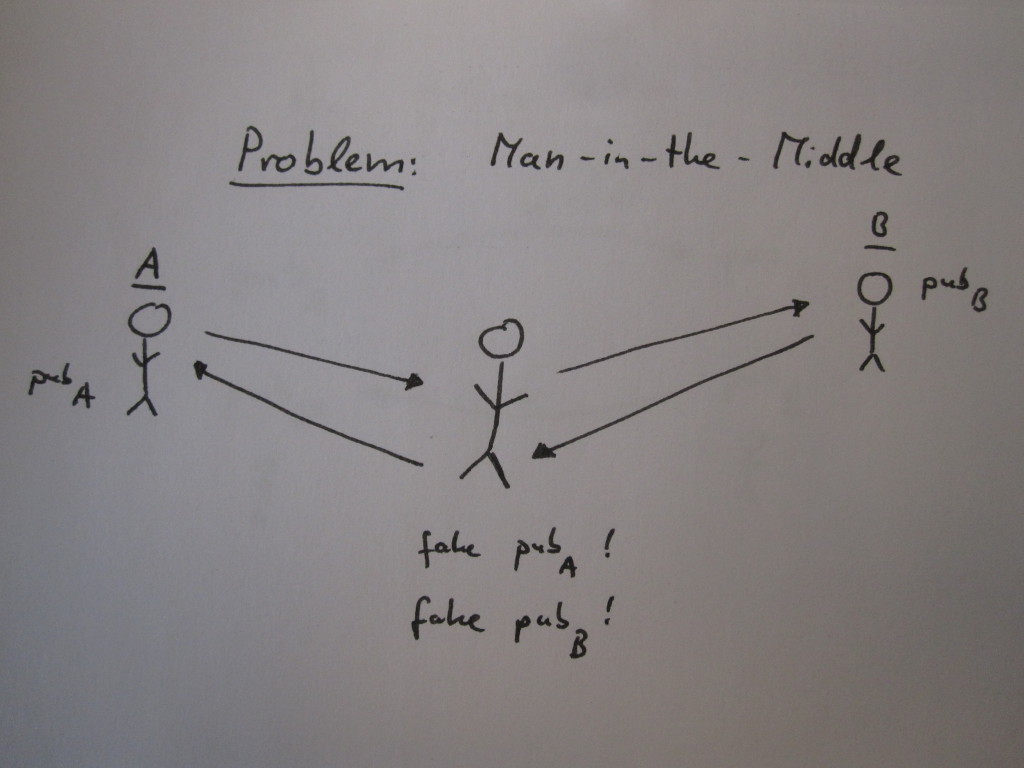 The Socialist Millionaires' Protocol
The Socialist Millionaires' Protocol
A zero-knowledge protocol developed by Boudot et al. enables the secret and secure comparison of two fingerprints over an insecure channel. The communicating peers require only once a comparatively weak shared secret. [translated]
Presentation about the mathematical background behind a cryptographic system that is used in practice but not wide-known. (German)
Prepared as classwork for a seminar in mathematics.
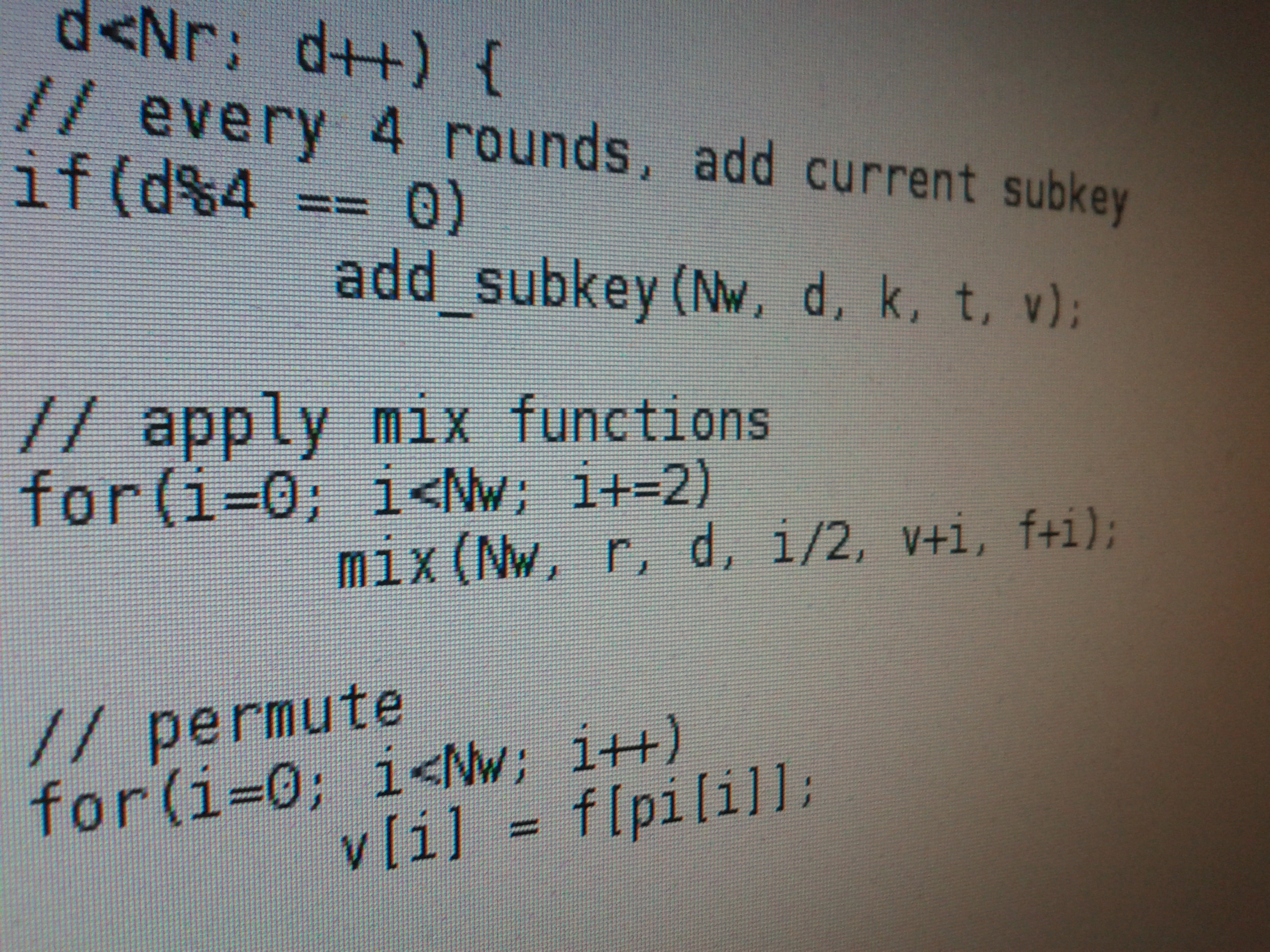
Skein 512in 256 lines
Skein is a new family of cryptographic hash functions. Its design combines
speed, security, simplicity, and a great deal of flexibility in a modular
package that is easy to analyze.
Development of as short and readable a C implementation as possible
of the Skein
Hashfunktion by Schneier et al., one of the final
candidates in the competition for the standardization of SHA-3.
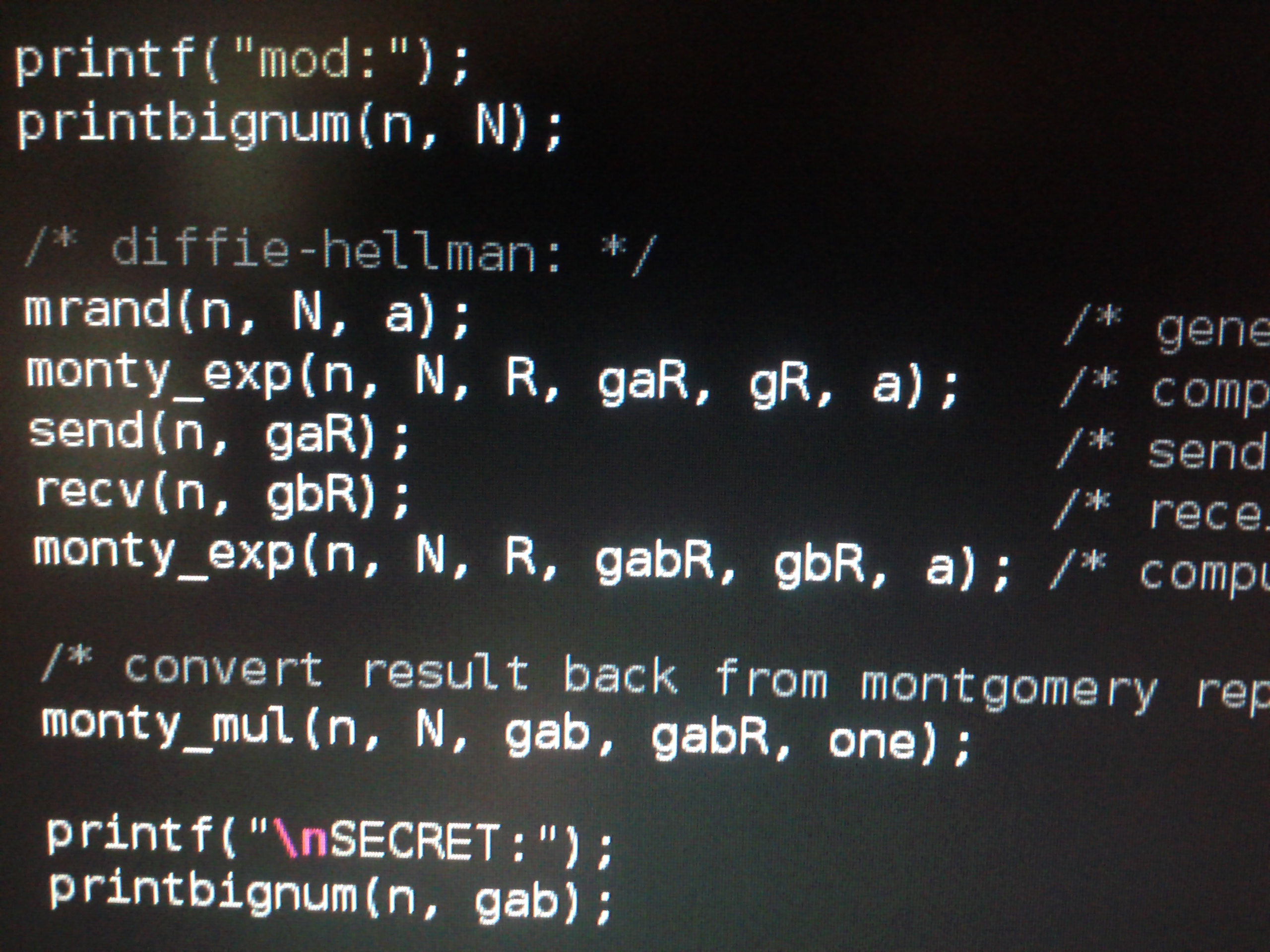
Diffie-Hellmanin 200 lines
Of course Diffie-Hellman really is pretty simple. Five lines.
All you need is exponentiation. No problem.
There is square-and-multiply for that.
Easy peasy, as long as you can multiply ... modulo large primes.
[translated]
Development of as short and readable a C implementation as possible of the Diffie-Hellman protocol, using the Montgomery method for multiplication in large residue class rings.